Nmap Scan Ip Range Hostname

Nmap 192 168 10 4 specify a scan range of ips using a subnet notation.
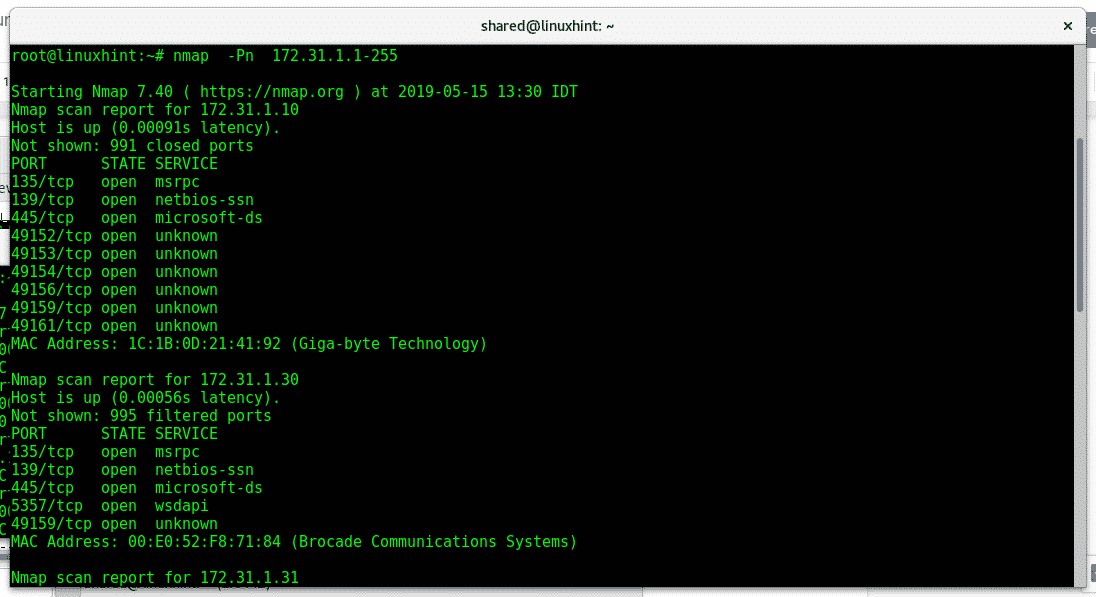
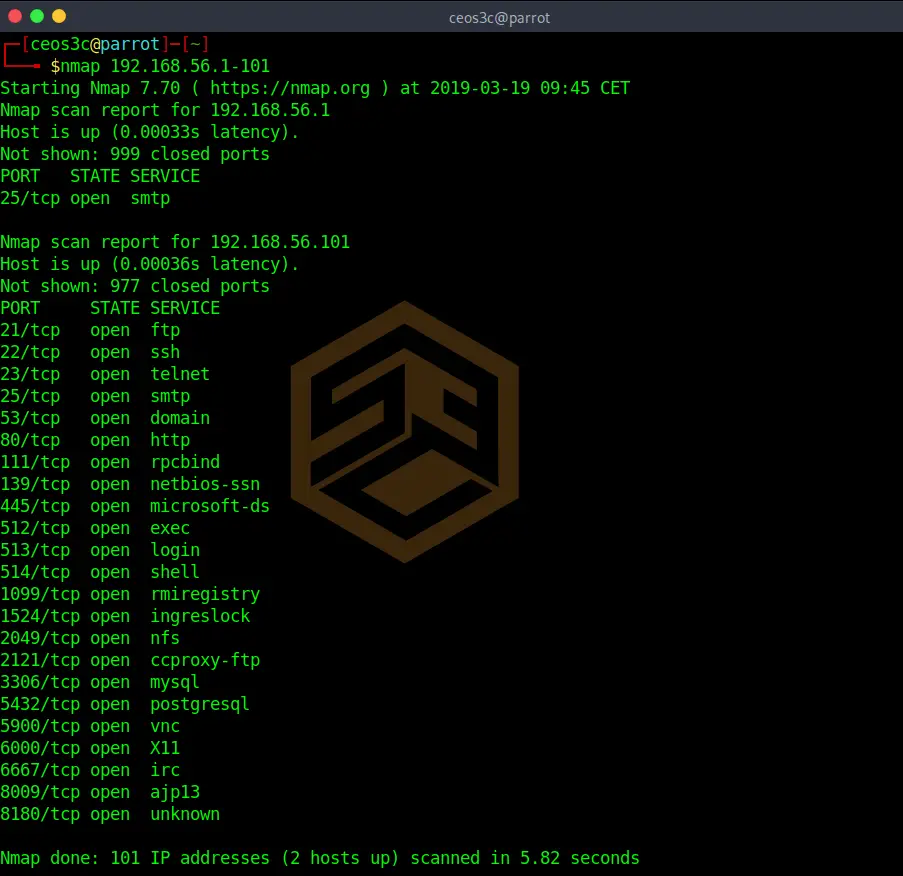
Nmap scan ip range hostname. Replace with the appropriate ip address to scan on your. Qualora si abusasse di questo servizio questo verrà disattivato e nmap riporterà il seguente errore. To scan a range of ip addresses 1 10. This is the basic format for nmap and it will return information about the ports on that system.
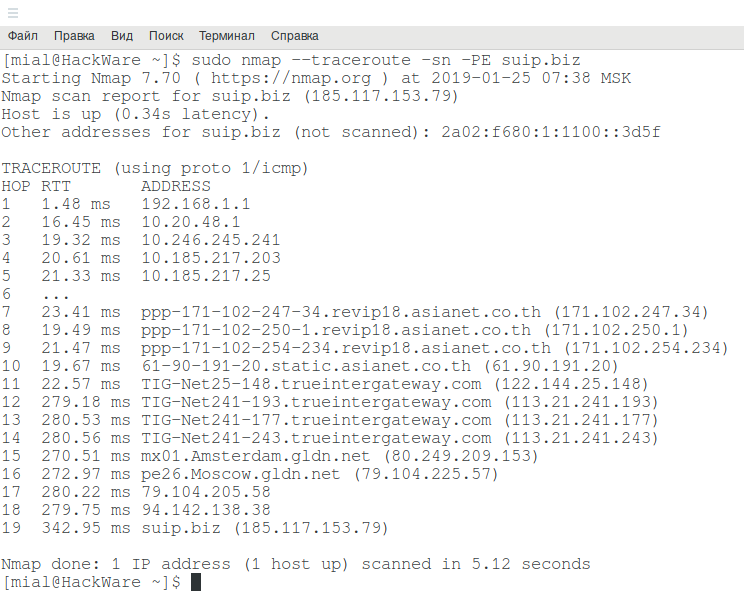
The name stands for network mapper but it s more of a port mapper. Each entry must be separated by one or more spaces tabs or newlines. You can use a nmap command to scan a single server using a host name such as server1 cyberciti biz or an ip address such as 192 168 1 254. Scanning ip ranges with nmap network mapper network scanner is easy thanks to nmap s flexibility.
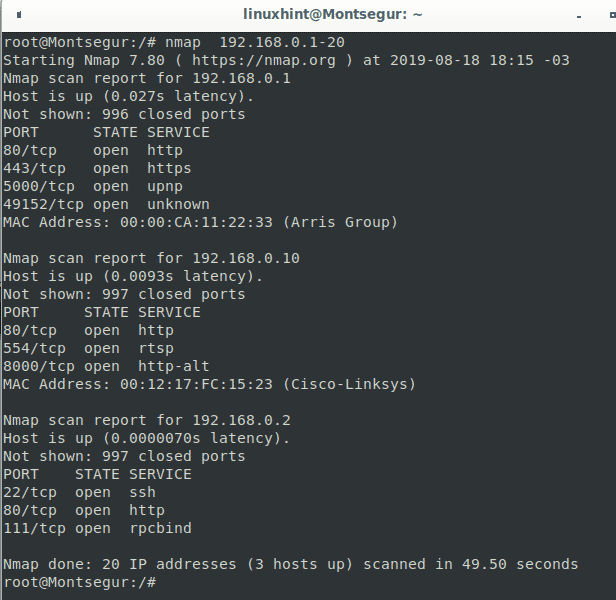
To run nmap on a subnet. This will scan 14 consecutive ip ranges from 8 8 8 1 to 8 8 8 14. In addition to scanning by ip address you can also use the following commands to specify a target. The simple default scan above will check the 1000 most well known ports for each ip address.
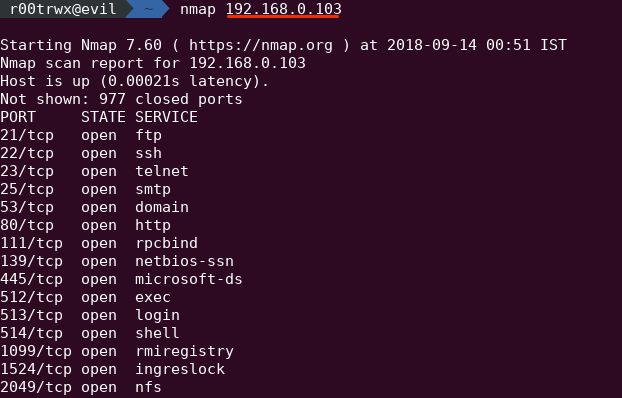
H ow do i use nmap command to scan a single server using a host name or an ip address under unix like operating systems. Although this is a gui based tool it also comes with a command line version that you can use if for instance you want to include the tool s functionality in your scripts. This tutorial focuses on all these methods. Nmap is built to scan a provided hostname or network address and return a list of open ports.
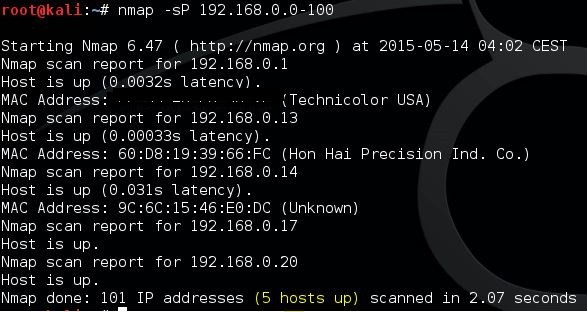
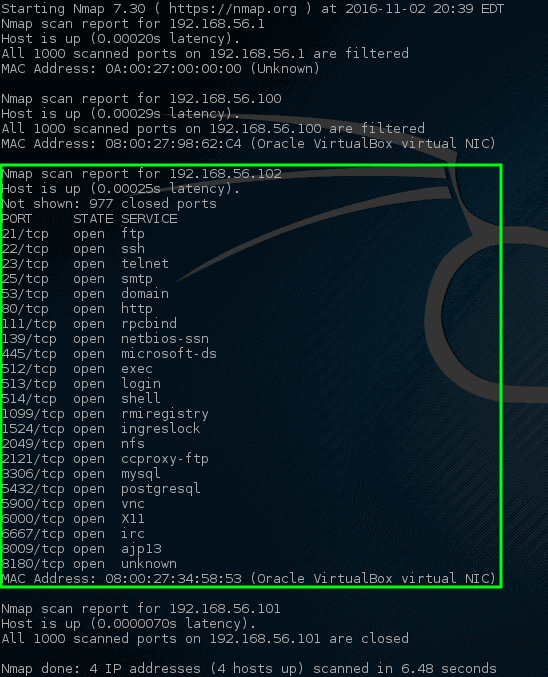
What if you want to scan all ports of the ip range under scope. Simply generate the list of hosts to scan and pass that filename to nmap as an argument to the il option. You can also use nmap to scan entire cidr ip ranges for example. Simply include the targets comma separated or as a list with line breaks.
Enter a public ip address or hostname that is accessible from an external internet facing perspective. The angry ip scanner can not only scan complete networks and subnets but also an ip addresses range or a list of ip addresses from a text file. Failed to resolve given hostname ip. An alternative is to simply use this kind of range.
You can scan single targets whole subnets partial subnets file lists with targets you can even instruct nmap to generate random targets or to discover possible targets within a network based on specific conditions or arbitrarily. 3 specify a scan range of ips using a wildcard. Nmap 8 8 8 this will scan. Scan all ports of an ip range.
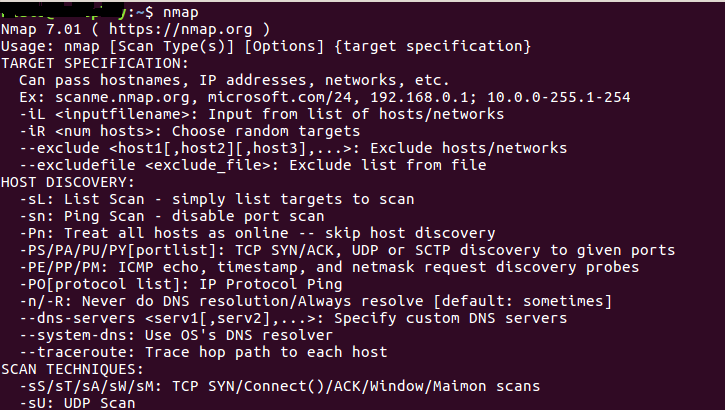
You can even use wildcards to scan the entire c class ip range for example. To scan a host. Entries can be in any of the formats accepted by nmap on the command line ip address hostname cidr ipv6 or octet ranges.