Nmap Scan Ip Range Port 80
You can also use nmap to scan entire cidr ip ranges for example.
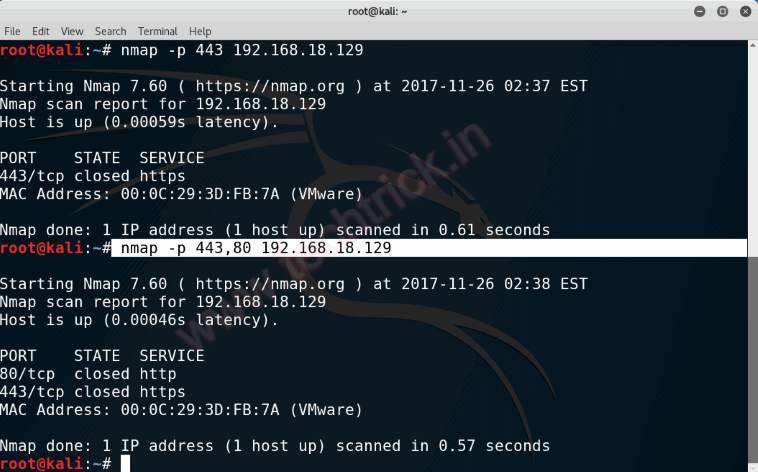
Nmap scan ip range port 80. An alternative is to simply use this kind of range. To scan nmap ports on a remote system enter the following in the terminal. You can even use wildcards to scan the entire c class ip range for example. Nmap vvv sn 201 210 67 0 24 you can also specify a specific range like this.
Nmap sp 201 210 67 0 100. Nmap is netmask aware. Nmap comes with a nice output parameter og grepable output which makes parsing more easy also it is not necessary to iterate through all ip addresses you want to scan. Simple nmap scan of ip range.
To scan a class b network specific range we use the same method implementing a hyphen in the last 2 octets. Go ahead and scanme. Today we re going to extend your port scanning knowledge by sharing the top 20 and 200 most popular ports recognized in the infosec industry. Scan an entire ip range.
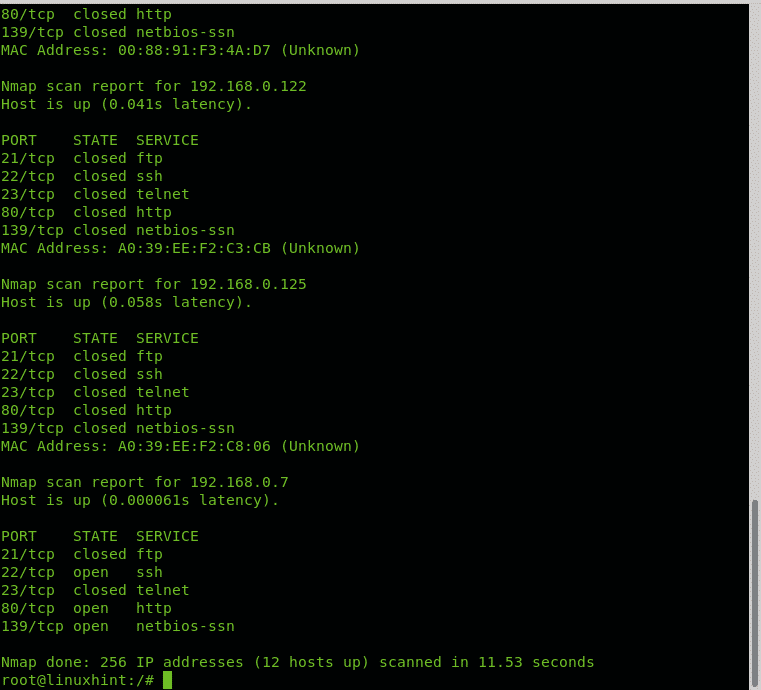
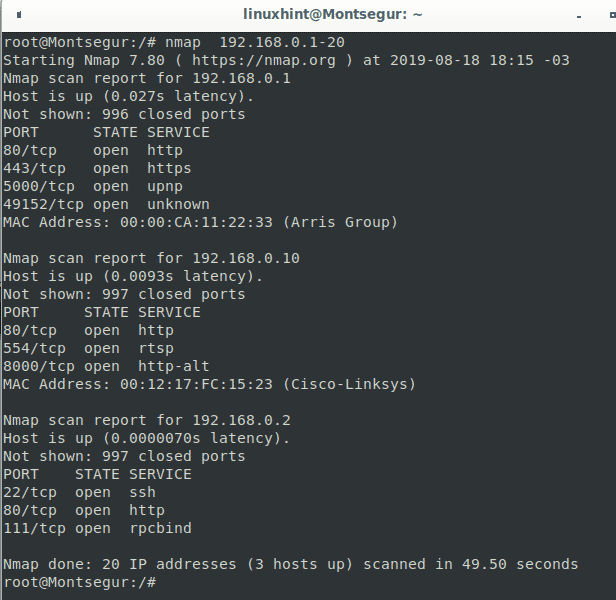
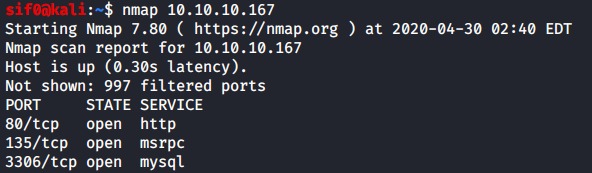
113 tcp closed auth device type. Based on nmap online it performs accurate port discovery and service detection. In this default scan nmap will run a tcp syn connection scan to 1000 of the most common ports as well as an icmp echo request to determine if a host is up. Nmap scanned for available hosts on addresses going from 192 168 0 1 to 192 168 0 30 finding 3 devices within the instructed range nmap shows their opened ports from the most common 1000 ports.
This will scan 14 consecutive ip ranges from 8 8 8 1 to 8 8 8 14. In addition to scanning by ip address you can also use the following commands to specify a target. Nmap 8 8 8 this will scan. The scanner allows you to easily map the network perimeter of a company check firewall rules and verify if your services are reachable from the internet.
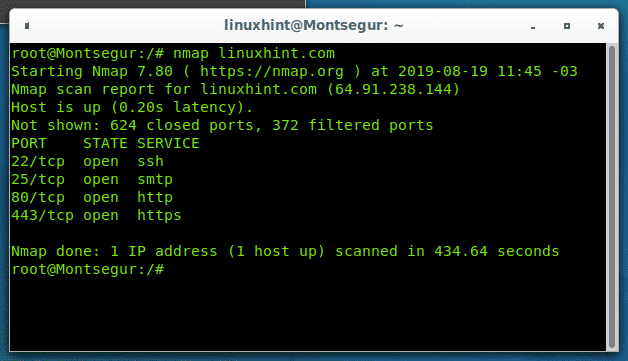
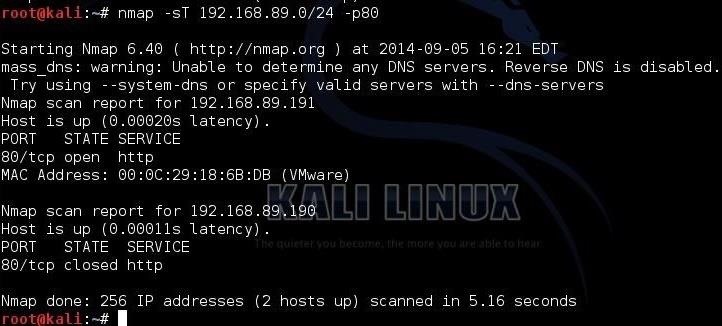
So it speeds up the process. You might find that a site has several machines on the same ip range. The default scan of nmap is to run the command and specify the ip address es without any other options. Nmap p80 192 168 0 0 24 og grep 80 open.
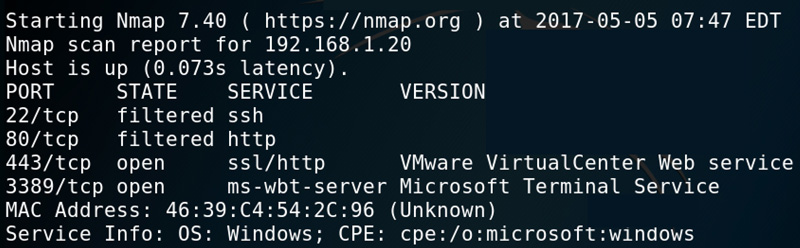
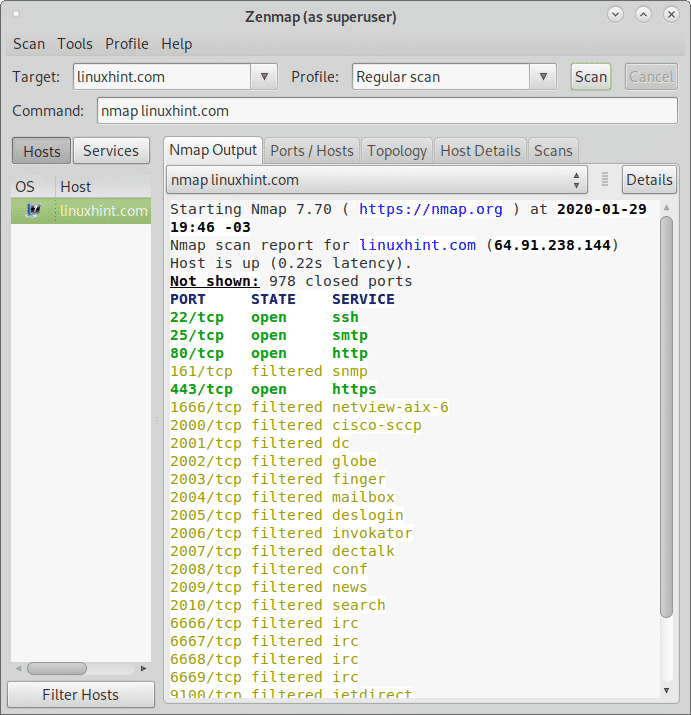
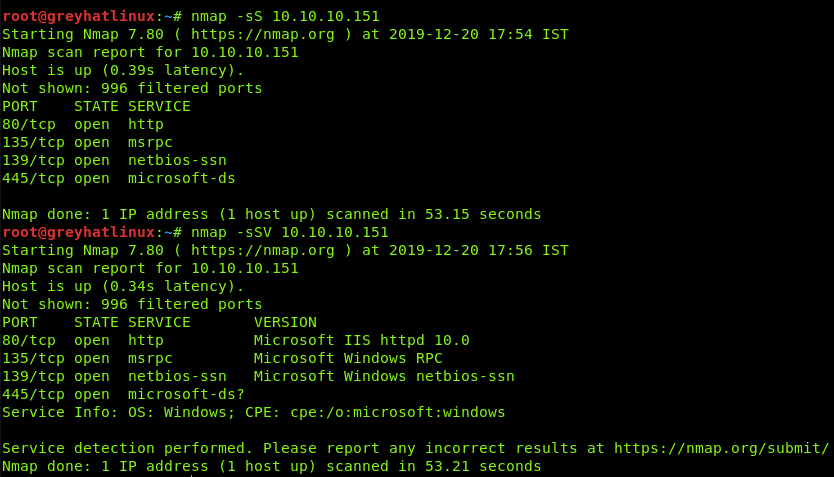
65530 filtered ports port state service version 22 tcp open ssh openssh 4 3 protocol 2 0 25 tcp closed smtp 53 tcp open domain isc bind 9 3 4 70 tcp closed gopher 80 tcp open http apache httpd 2 2 2 fedora html title. Your example can be written as. Detects open tcp ports running services including their versions and does os fingerprinting on a target ip address or hostname. In previous posts we ve written about the best port scanners and covered the most popular nmap commands to scan remote hosts all to improve your port scanning daily tasks.
The sn flag stops nmap from running port scans.