Nmap Scan Ip Range Ssh

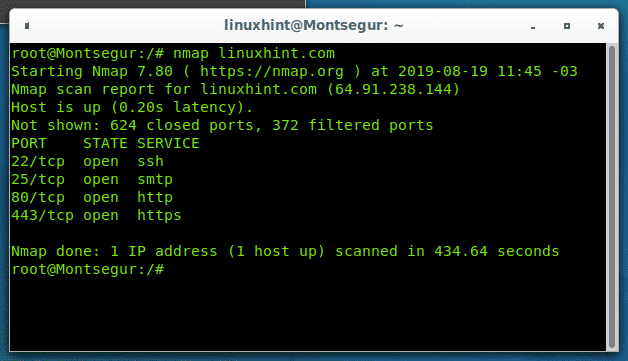
The simple default scan above will check the 1000 most well known ports for each ip address.
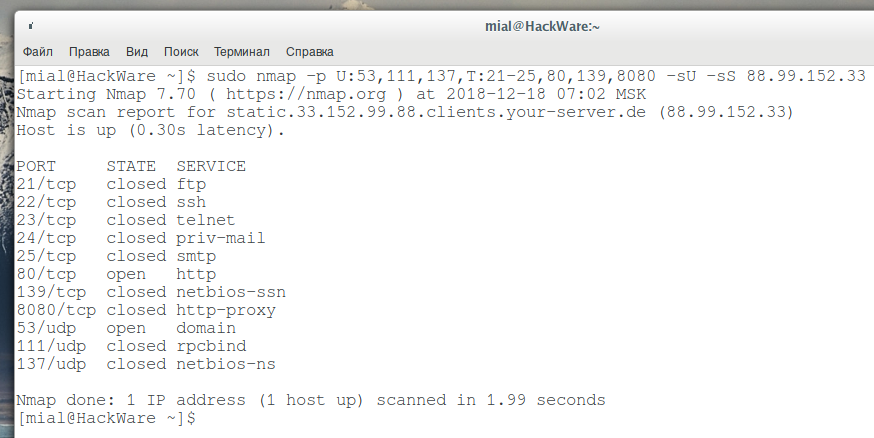
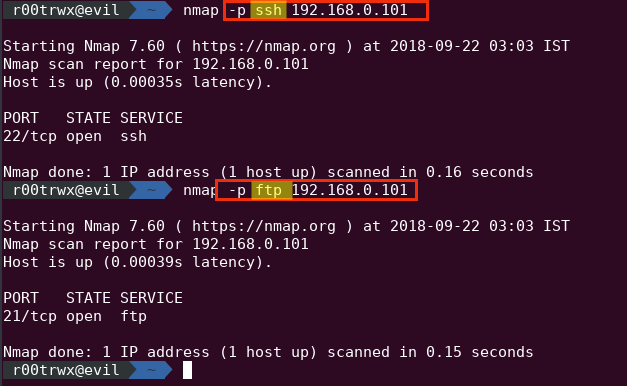
Nmap scan ip range ssh. To symcbean s question it was easy to know the correct pc based on the mac address decoding automatically done by nmap zenmap to the motherboard manufacturer and the operating system used. For the first connection i wanted to find the ip without carrying a keyboard and monitor over to it. Replace the ip address with the ip address of the system you re testing. Nmap p 22 open sv 10 0 0 0 24 sshservers.
Here s a simple example that will scan all computers on your 255 255 255 0 subnet and report any devices listening on port 22 the default for ssh. You can also use ranges to scan multiple. All of this along with the version of ssh that the server is running is output to a text file sshservers. Nmap which stands for network mapper is an open source tool that lets you perform scans on local and remote networks nmap is very powerful when it comes to discovering network protocols scanning open ports detecting operating systems running on remote machines etc the tool is used by network administrators to inventory network devices monitor remote host status save the scan results.
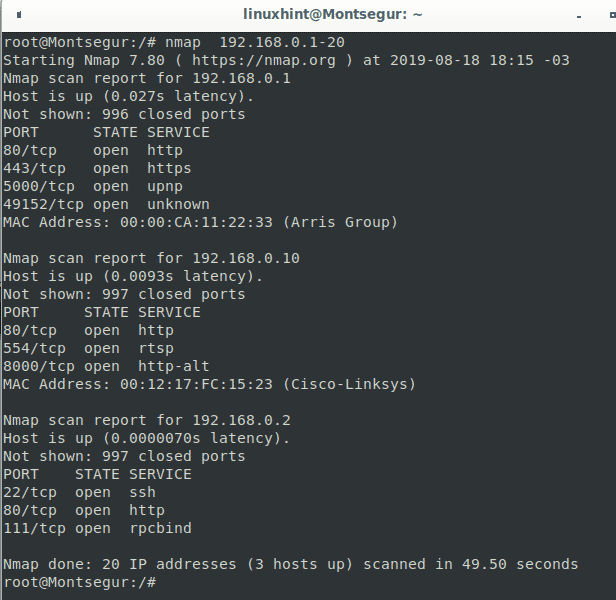
Nmap 192 168 10 4 specify a scan range of ips using a subnet notation. 3 specify a scan range of ips using a wildcard. This one is handy if you are verifying that none of your devices are running ssh v1. In addition to scanning by ip address you can also use the following commands to specify a target.
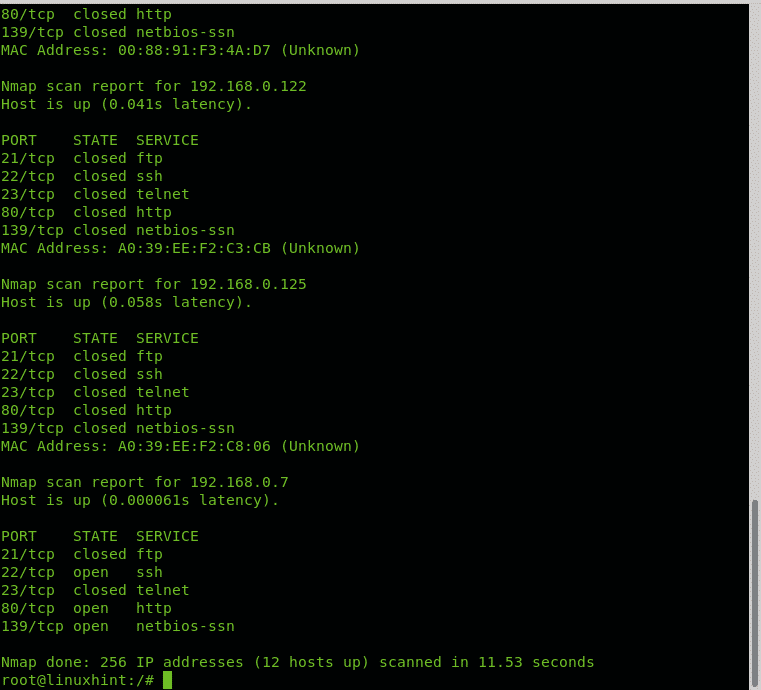
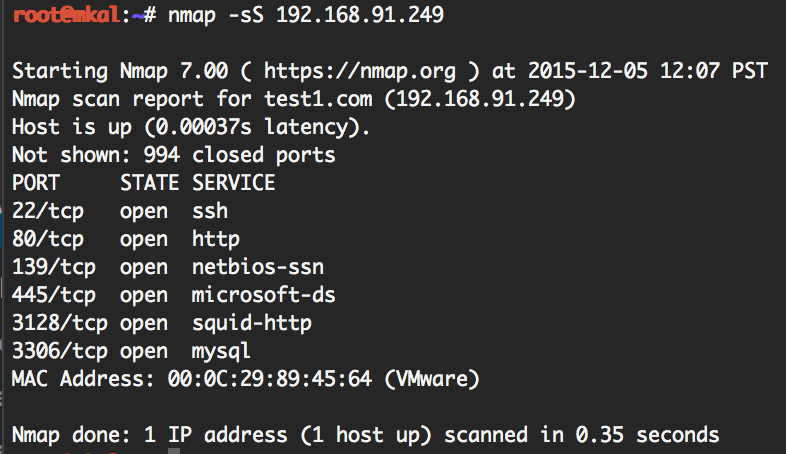
22 tcp open ssh 111 tcp open rpcbind 139 tcp open netbios ssn 445 tcp open microsoft ds nmap done. 100 ip addresses 2 hosts up scanned in 25 84 seconds scanning a range of ip addresses in this example nmap is instructed to scan the range of ip addresses from 192 168 10 1 through 192 168 10 100. Nmap 8 8 8 this will scan. You can even use wildcards to scan the entire c class ip range for example.
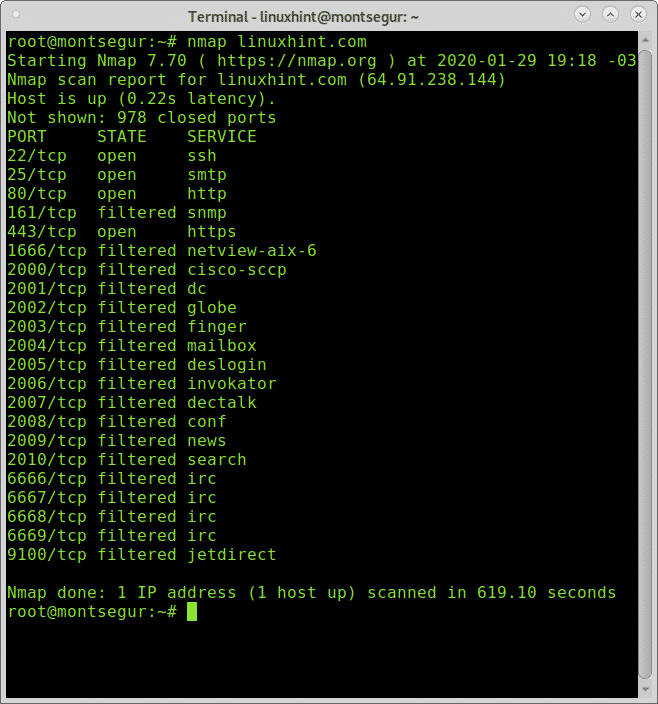
Note that we re not providing nmap with an ip range. You can also use nmap to scan entire cidr ip ranges for example. What if you want to scan all ports of the ip range under scope. This is the basic format for nmap and it will return information about the ports on that system.
Sometimes you don t know the ip and need to find it. Scanning ip ranges with nmap network mapper network scanner is easy thanks to nmap s flexibility. This tutorial focuses on all these methods. An alternative is to simply use this kind of range.
997 closed ports port state service 22 tcp open ssh. We re focussing nmap on a single ip address which is the ip address of the device in question. This will scan 14 consecutive ip ranges from 8 8 8 1 to 8 8 8 14. To scan nmap ports on a remote system enter the following in the terminal.
On the machine used to research this article it took nine minutes for nmap to execute that command. Remember nmap can scan a range of ip addresses not just one host. Nmap scan report for 192 168 10 50 host is up 0 053s latency. Nmap script banner 192 168 10 50.
Sudo nmap a t4 192 168 4 11. Scan all ports of an ip range.